The workbench includes a wizard that build a monitoring application for the open project. The monitoring application is operated by the Monitoring Tool for spying and controlling the project without need of a full Workbench. Run the "Tools / Build monitoring application" from the menu of the main window to start the wizard.
Notes: Depending on your license, the wizard may not be available.
Main principle:

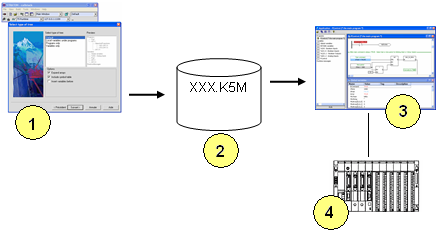
The Workbench (1) is used for building the monitoring application in a unique file (2). The standalone Monitoring Tool (3) operates the monitoring application: it animates documents according to real time values from the connected target runtime (4). A monitoring application groups programs, lists of variables, plus the trace of runtime messages. The tool displays the value of the variables and can be used for forcing a variable. The set of items available in the monitoring application is selected in the wizard when building the application. Below is the description of the following operations you must perform when using the wizard:
Identification of the monitoring application
The first step is to give a name to your application. This name will be displayed in the main title bar of the viewer. The configuration of a monitoring application can be saved on the Workbench project. You can select to reopen an existing configuration in this page.
Type of projects tree and main options
The following step consists in setting main options for the application. The list of visible items will be shown as a tree in the viewer. You can choose among various presentations for the tree.
If you check the "Include symbol table" option, the monitoring application willl work on the full symbol table generatedby the compiler. You must take care that the same version of the application is running on the target. If you don't select this option, then the monitoring tool will automatically upload symbols from the target at connection time. In that case, you must ensure that all used symbols are embedded in the runtime application.
Selecting items
The next step is to select all the items of the project that you want to include in the monitoring application.
Passwords for items
For each item included in the application you can define a password so that the corresponding document will be protected in the monitoring application.
Passwords for variables
You can define passwords for the Monitoring Tool to make write
access (forcing) to runtime variables. For each variable you can
select one of the following access protection:
- Free : the variable can be freely forced
- Protected : forcing the variable is possible with a password
- No : the variable can never be forced.
Simply drag variables from the list at the bottom to the upper list to set its protection mode. The "Default" choice indicates the protection mode that should be applied to all variables not explicitely expressed in the upper list.
Destination file
Everything is now ready for generating the monitoring application. The next step prompts you for selecting the pathname of the file that will contain the monitoring application. The application is stored as a unique compressed file.
The end
Now the application is generated. You can run it in simulation mode in the last page of the wizard. This page also proposes you to save the current configuration of the application so that you can use it later for update purpose.
Security issues
All programs stored in the monitoring application are encrypted. The user of the viewer cannot explore, copy or drag the contents of a watched program.