There are various methods for implementing security of Web-based applications. The approach that you require can depend on a number of factors, and may involve one or more methods of implementing Security.
Method 1: Password Protection

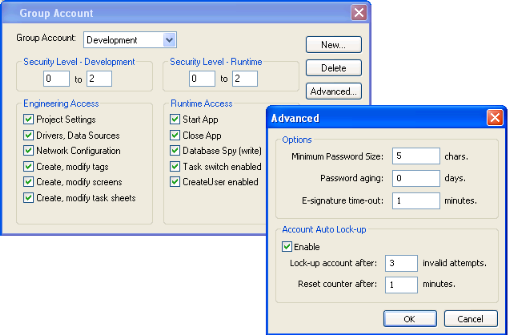
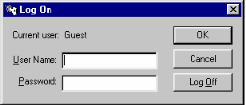

For more information, see Security.
Method 2: Disabling Thin Client Commands
IWS allows bi-directional data exchange between the Thin Client and the Data Server. However, for security reasons it may be advantageous to only allow the Thin Client to view the process or machine data, and not send any data back to the Data Server.
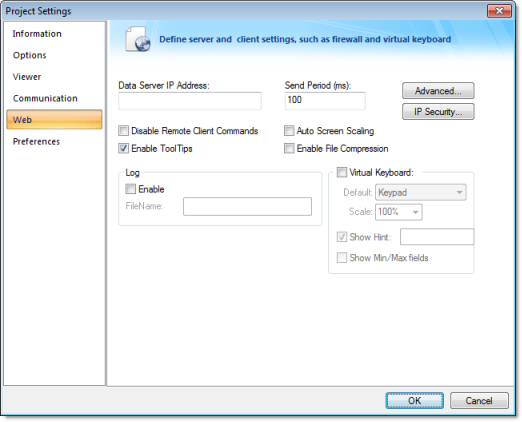
Method 3: Embedded Firewall
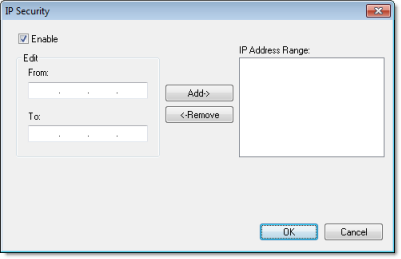
This feature allows the user to filter access to the project based on the Thin Clients IP Address. When a Thin Client attempts to connect to the Server station, the Server checks if the IP Address of the Thin Client station is authorized to access the project. The ranges of authorized IP Addresses can be configured in the Server station by clicking IP Security in the project settings (Thin Client on the Project tab of the ribbon):
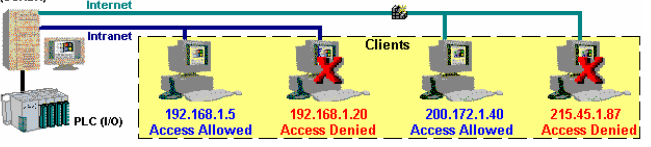
Method 4: Encrypted Communications (SSL)
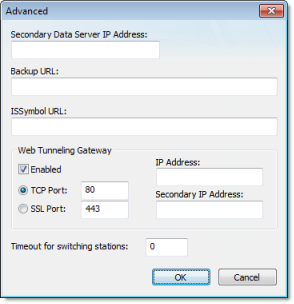
- Click Advanced in the
project settings (Thin Client on
the Project tab of the ribbon). Select (check) the Web Tunneling Gateway Enabled option. Click
on the SSL radio button and be sure
the SSL port is set to 443. Click OK.
Figure 7. Project Settings — Web — Advanced dialog
- In your Web Server, be sure SSL capabilities are enabled and that a SSL Certificate of Authentication is present.
- Be sure SSL is enabled in the Web Client
- Set up all other Web configurations to support the WTG.
Method 5: VPN
A VPN is a Virtual Private Network. It is called virtual since it really uses the public Internet to transport data from one computer to another. But since this network is encrypted and uses other security mechanisms enabled by the ISP, is it a very secure Private Network. While VPN's are inherently secure, they are more costly that a simple public Internet connection.